Public key cryptography, often known as asymmetric cryptography, is used to create digital signatures. Two keys are produced using a public key method like RSA (Rivest-Shamir-Adleman), resulting in a mathematically connected pair of keys, one private and one public.
The signer must have complete control over the data used to produce the e-signature at the moment of signing.
Any change to the attached e-signature or the document to which it is attached must be traceable (tamper-evident seal).
An audit trail should be kept that outlines the procedures followed during the signing process.
A Certifying Authority (CA) authorized by the Controller of Certifying Authorities (CCA) must issue the digital signature certificate.
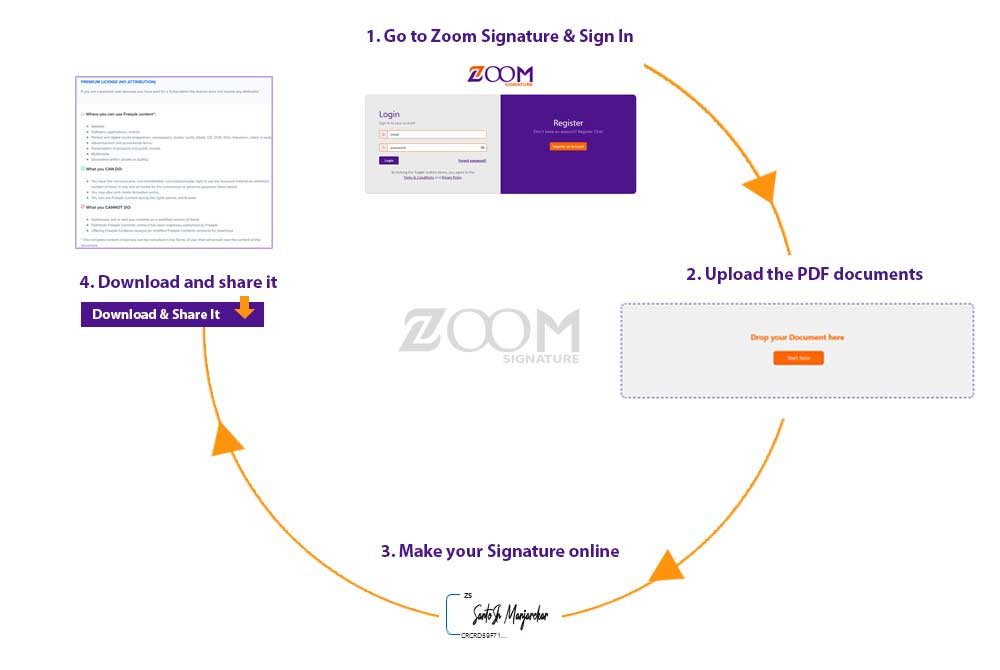
You may be asked to provide certain information depending on the Certificate Authority you are using. There may also be constraints on which you may send papers to for signature and in what sequence you can transmit them. The UI of ZOOM Signature guides you through the process and guarantees that you fulfill all of these standards.
ZOOM Signature makes it easy and secure to get your documents signed digitally.